
In a recent webinar, Dr. James Stanger, Chief Technology Evangelist at CompTIA and member of the Forbes Technology Council, delved into the challenges faced by technologists and the paradigm shifts occurring to address these challenges. As cybersecurity trends and environments evolve, it's crucial for professionals to adapt and acquire the skills necessary to navigate this complex environment.
Key realizations in the tech industry
Dr. Stanger highlighted several key realizations that industry leaders are embracing:
Multiple architectures in organizations
Organizations operate with various architectures, including business, application, data, and technology. Dr. Stanger emphasized the importance of prioritizing business architecture, as it forms the foundation for effective technology implementation.
Beyond vendor solutions
Protecting the attack surface requires a shift from relying solely on vendor products. Leaders are recognizing the need for a deeper understanding of attack lifecycles and system interconnections, moving beyond checkbox-oriented approaches.
The need for wise assistants
Quoting Denise Zheng, Chief AI Officer and Data Lead at Accenture, Dr. Stanger noted the value of having even a mediocre assistant for overworked cybersecurity professionals. Assistance can alleviate the burden and enhance efficiency.
Toxic combinations
Organizations face challenges when new technologies are paired with outdated processes. The emergence of "Shadow AI," where generative AI is used without proper security policies, poses significant risks. Such toxic combinations can be as detrimental as SQL injections or supply chain attacks.
These challenges and their solutions are detailed in the CompTIA State of Cybersecurity 2025 report.
Overcoming challenges by embracing new paradigms
Fortunately, the cybersecurity industry is witnessing paradigm and process shifts that help address these challenges.
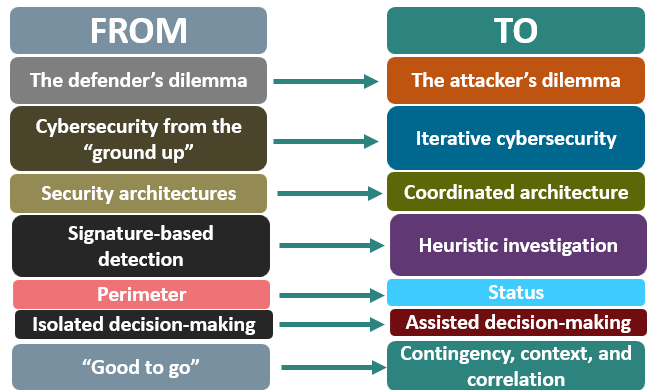
For example, while the “Secure by Default” / “Secure by Design” approaches are useful, organizations are finding that iteration is vital; this paradigm change helps organizations focus on constant, documented improvement of processes.
The second approach is where organizations find opportunities to empower their workers with unique skills combinations. James noted that organizations today are looking for people with many skills. Top technical skills included:
Incident response
Developing the ability to react decisively during cybersecurity events.
Security analytics
Identifying toxic combinations and creating queries for datasets, such as Splunk queries.
Infrastructure as code (IaC)
Using code to launch, update, and secure systems.
Security as code (SaC)
Providing developers with integrated processes, tools, and platforms.
Automation
Utilizing tools from simple scripts to Kubernetes.
Network micro-segmentation
Enabling zero trust environments to thrive.
Operational technology (OT) security
Managing and securing OT solutions within IT departments.
By embracing these new paradigms and skills, professionals can effectively navigate cybersecurity challenges and avoid toxic combinations that threaten organizational security. As the field continues to evolve, staying informed and adaptable is key to success.
The soft skills that drive tech careers
In addition to technical skills, James highlighted the importance of certain soft skills that are consistently valued by techies and leaders in the cybersecurity workforce. Over the past year, whenever he inquired about the most critical skills, the following attributes were frequently mentioned:
Curiosity
The drive to explore, question, and seek out new knowledge.
Empathy
The ability to understand and share the feelings of others, fostering better communication and collaboration.
Willingness to learn
An openness to acquiring new skills and adapting to change.
James also shared insights from various tech leaders around the world, including Andy Flatt, a CIO based in Nashville, Tennessee. Mr. Flatt emphasized that he learned about the importance of curiosity and empathy by engaging with stakeholders and listening attentively. He also echoed a sentiment shared by tech leaders from the University of Cambridge, Oxford University, and Glasgow University: the need to respect three fundamental "time zones":
1. The past: Honor what has happened before by studying it carefully. Understanding historical context can provide valuable lessons and insights.
2. The present: Focus on the current situation. Being present and attentive to current challenges and opportunities is crucial for effective decision-making.
3. The future: Have a clear goal and focus on equipping workers with the skills needed to achieve that goal. Forward-thinking and strategic planning are essential for long-term success.
For instance, the CIOs from Cambridge, Oxford, and Glasgow recognized the importance of honoring the past by helping their workers compare their current mindsets to the cloud-oriented future they envisioned. They achieved this through hybrid training programs and focus group sessions, where workers could discuss their insights and experiences during the training process. This approach not only facilitated skill development but also encouraged a culture of continuous learning and adaptation.
Making workers more human
Dr. Stanger shared a pivotal insight from his conversations with IT leaders worldwide: the most sought-after workers possess unique combinations of both soft and technical skills. It's impossible to isolate these skill sets from one another. This integration is what makes education so transformative for organizations. By providing a space where workers can develop both critical soft and technical skills, education helps create uniquely capable individuals.
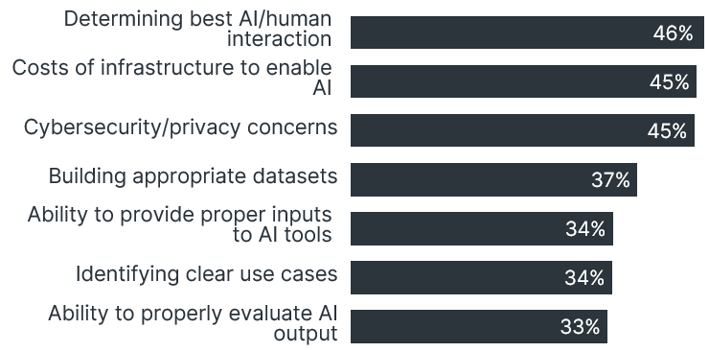
Dr. Stanger emphasized that the most progressive organizations are those that are actively helping their workers with AI collaboration. According to the CompTIA Building AI Strategy report, successful organizations are exploring how to optimize AI and human interactions. This approach not only enhances productivity but also ensures that workers remain integral to the technological advancements within their organizations. By fostering an environment where AI and human skills complement each other, organizations can drive innovation and maintain a competitive edge in the industry.
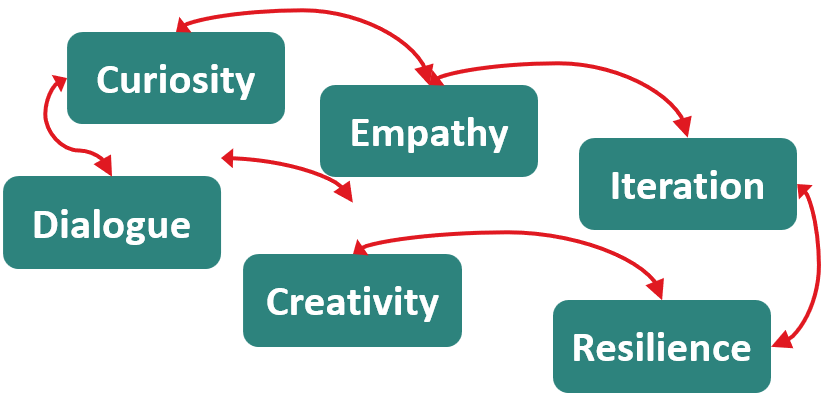
This, Dr. Stanger pointed out, begs the question about what really makes us human. He pointed out that in addition to curiosity and empathy, humans have gifts for iteration, dialog, creativity, and resilience.
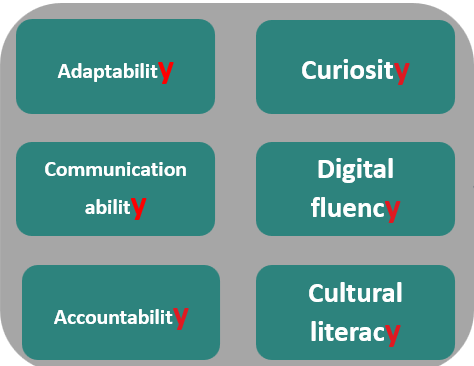
But, when a new technology appears, we sometimes forget what it means to be properly human. We sometimes default to what Dr. Stanger calls the “Copy and Paste (CAP) model.” That’s somewhat natural, he noted. But, to become more human, it’s vital to engage AI in a productive dialogue. Part of that dialogue involves combinations of skills that involve digital fluency, adaptability, and advanced skills.
How educators can instill critical, unique skills combinations
The primary way to move forward is to focus on hands-on, practical activities. That’s the best way to create conditions where students learn about the critical skills combinations that help organizations avoid toxic business and tech combinations. Students can also check out CompTIA research, including the Building AI Strategy report and the CompTIA State of Cybersecurity 2025 report to find the ways organizations around the world are working to move the needle when it comes to using tech in a responsible way.
You can watch Dr. Stanger's insightful webinar Current Cyber Trends Your Students Need to Know on demand here.

