 Microsoft Active Directory (AD) is a directory service that offers centralized authentication and authorization (access control). While the focus is usually on the security words authentication and authorization, I suggest launching your journey into AD with the idea of centralization.
Microsoft Active Directory (AD) is a directory service that offers centralized authentication and authorization (access control). While the focus is usually on the security words authentication and authorization, I suggest launching your journey into AD with the idea of centralization.
A directory service enables administrators to manage user accounts, groups, computer accounts, devices and other nodes in a central location. This approach greatly simplifies administration tasks. If a user needs a password reset, a name change or resource access modifications, the administrators can accomplish these tasks by accessing one database (be aware that there are multiple copies of this database, but the concept is that there are several copies of the same repository). Centralization is a critical concept with Active Directory.
Authentication and authorization are certainly important. Here is a summary of the two terms:
- Authentication: Proving your identity to the network
- Authorization: Using that identity to gain (or be denied) access to resources
Users have one account with one password to remember (single sign-on) to access multiple resources. That account identity acts as their credentials for the resources AD manages. With the integration of Azure AD (renamed Entra), these can include cloud services.
The basic administrative unit of Active Directory is the domain. AD domains serve as boundaries. Specifically, they encompass three functions:
- Administrative boundary: Domains allow AD environments to be separated into areas of responsibility for various administrators.
- Replication boundary: Domain information, such as user accounts, does not replicate outside the boundary.
- Security boundary: Security policies, such as password requirements, do not replicate beyond the domain's borders.
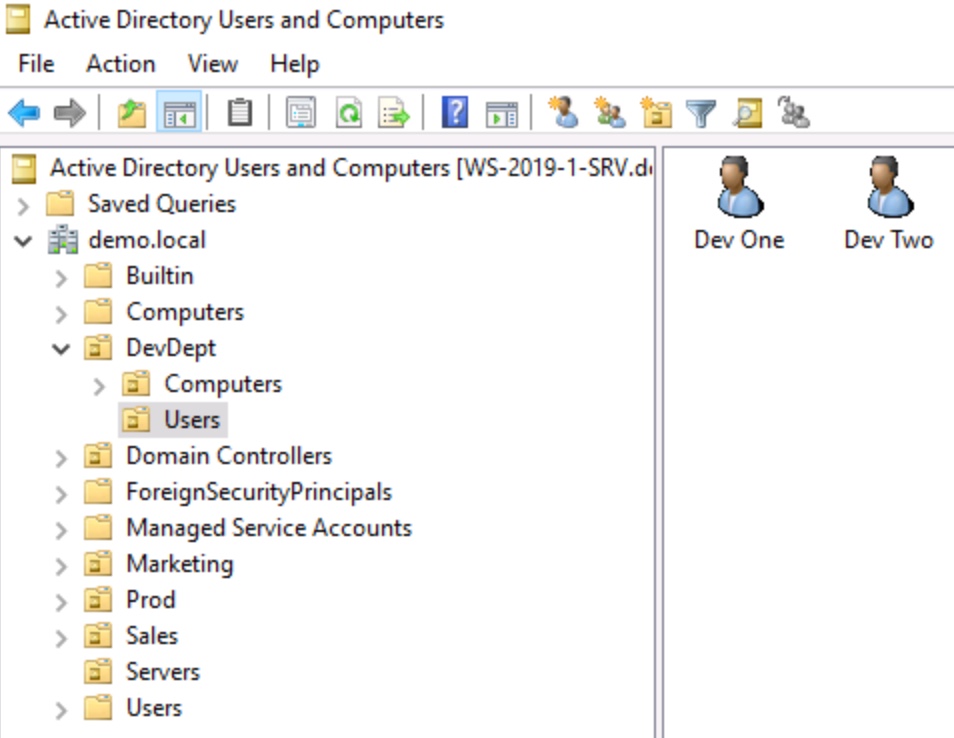
Figure 1: Active Directory Users and Computers is the primary administrative console, showing the domain (demo.local) and many OUs and containers.
How Does Active Directory Work?
At its heart, Active Directory is a database. Specifically, it stores objects made up of attributes. These domain objects include user and computer accounts created by administrators. They are used to manage authentication.
During the login process, your username and password are checked against what AD has on file. If the credentials match, you're authenticated and allowed on the network. If they don't, you're blocked.
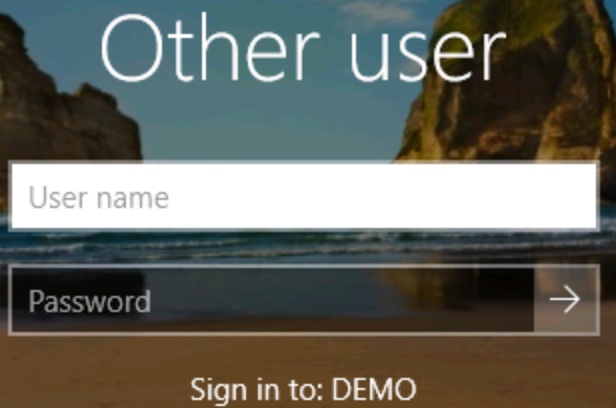
Figure 2: Login dialog box prompting for username and password, which will be confirmed by the DEMO domain.
Your Windows computer also has an account – and it even negotiates a password with AD! Not only is your identity as a user verified, but Active Directory also checks the computer's identity. During the authentication process, your workstation uses DNS to find the nearest Domain Controller (DC).
Active Directory is usually spoken of as one thing, but there are almost always at least two copies of the database. Domain Controllers host a copy of the AD database and act as authentication servers. Every domain should have at least two DCs for fault tolerance, but most environments will have many. For example, you will often find at least one DC at each branch office.
Figure 3: DNS console displaying the demo.local domain information stored in DNS.
When a user changes their password or an administrator creates/deletes a user account, the change happens on one DC – usually the one nearest the user or administrator. The changed attribute (such as a password) is then copied, or replicated, to all the other Domain Controllers. Within a very short time, all DCs have an updated copy of the changed object. This replication mechanism helps keep the databases consistent throughout the domain.
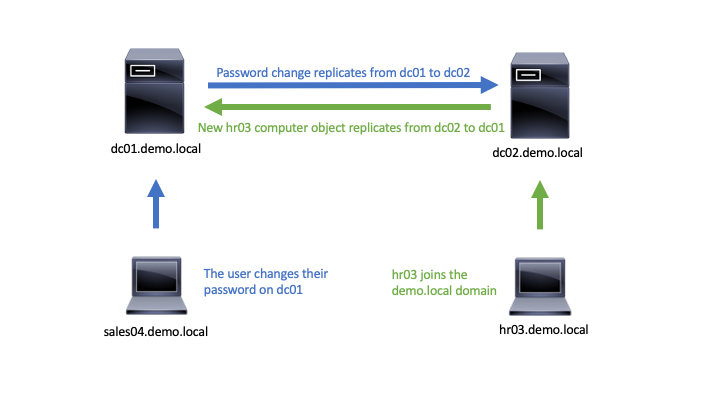
Figure 4: AD replication of changes between domain controllers, ensuring both have the same updated information.
Why Is Active Directory Important?
AD is a critical part of any Windows network environment. It even offers limited support for Linux and macOS systems. Many of Microsoft's core on-premises and Azure cloud services are built on top of the AD infrastructure. It has become a core component of most enterprise networks since its release in 2000.
Active Directory Components
Active Directory consists of many components. Any discussion should begin with domains. As mentioned above, domains are boundaries for administrative, security and replication control. Aspects of AD are either larger than a domain (tree and forest) or smaller than a domain (Organizational Unit).
Organizational Units (OU) are collections of users, computers and groups that allow for administration control and the application of Group Policy settings. Senior AD administrators can delegate administrative tasks to specific OUs for junior administrators.
User and computer accounts are AD objects to represent people and their devices. These objects allow administrators to identify and control the settings applied to signed-on users and systems. Controls might include password requirements, restricted access hours or the deployment of software such as Microsoft Office. Computers attached to an AD domain are said to be "domain members."
Administrators put user and computer objects into groups for easier control. Permissions are applied to the groups, granting access to resources. AD recognizes three types of groups:
- Domain local groups
- Global groups
- Universal groups
Each group has its own specific function.
Multiple related domains form a tree. An AD tree is a larger administrative unit that shares some naming properties but isolates replication traffic and security controls for administrative flexibility. Larger enterprises may combine multiple trees into a forest. These also allow administrative flexibility.
Group Policy is a built-in configuration management tool. Administrators choose among thousands of security, configuration, software and other settings to provide users with the tools they need to do their jobs. These settings are collected into Group Policy Objects (GPOs) that are applied to Organizational Units or the domain. Administrators can set department-specific configurations by applying a GPO to an OU, perhaps to deploy sales software to the SalesOU or engineering software to the EngineeringOU. Linking a GPO to the domain enables administrators to deploy settings that apply to all users and computers—maybe a firewall configuration or a standardized desktop interface.
Active Directory Versus Workgroups
With Active Directory objects stored in a single database, administrative tasks are centralized. AD can manage millions of objects. Smaller Windows networks are called Workgroups. While there is no technical limit on their size, the practical (and recommended) limit is ten computers. This limited size is because each computer maintains independent storage of any user (and password) that might access it.
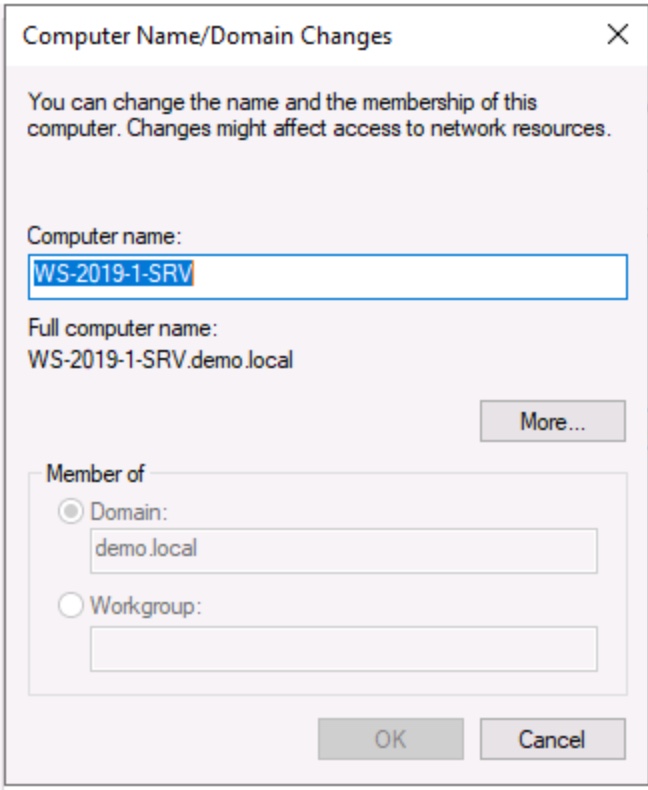
Figure 5: System Properties showing the option to make a computer a member of a domain or workgroup.
For example, suppose a small law office has eight computers and eight employees. The employees share the computers, so any employee can log on to any system. It's possible one employee could have a different username on each computer and that each account would have a different password associated with it.

Figure 6: Workgroup showing user kgarcia with different passwords on each computer.
As a Workgroup grows, it becomes more and more difficult to manage. Businesses with hundreds or even thousands of systems would be virtually unmanageable. Workgroups do not support centralized configuration management or security settings.
Active Directory Advantages and Disadvantages
The advantages of centralized administration, configuration management and authentication cannot be overstated. It's assumed in modern networks that single sign-on and access controls will be in place in whatever network you support.
Group Policy controls provide administrators with granular control over nearly every aspect of Windows systems.
Group Policy manages thousands of settings, including:
- Security settings
- Software deployments
- System configurations
- Desktop environments
- Browser settings
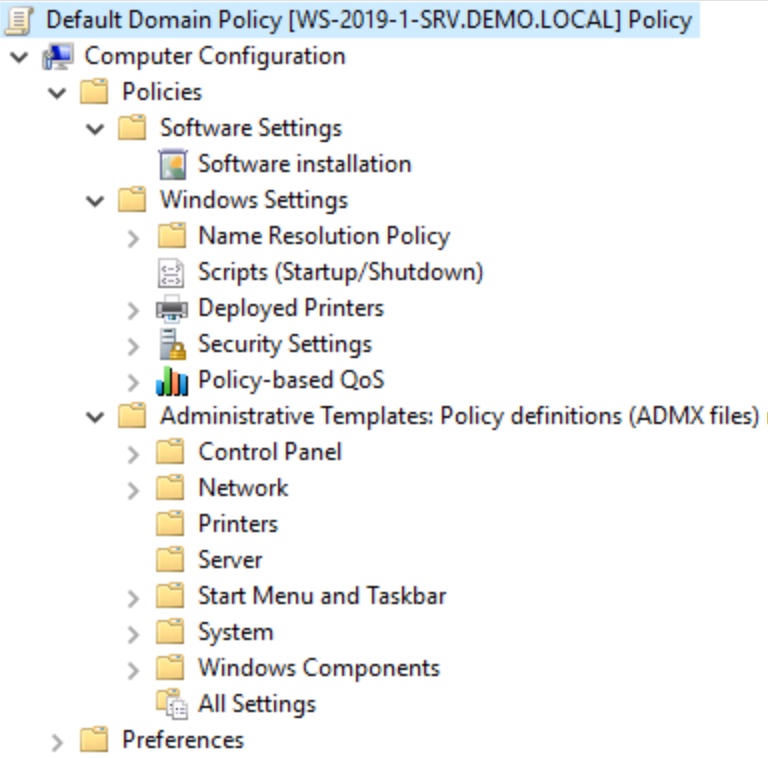
Figure 7: Group Policy console showing configuration management categories for computers.
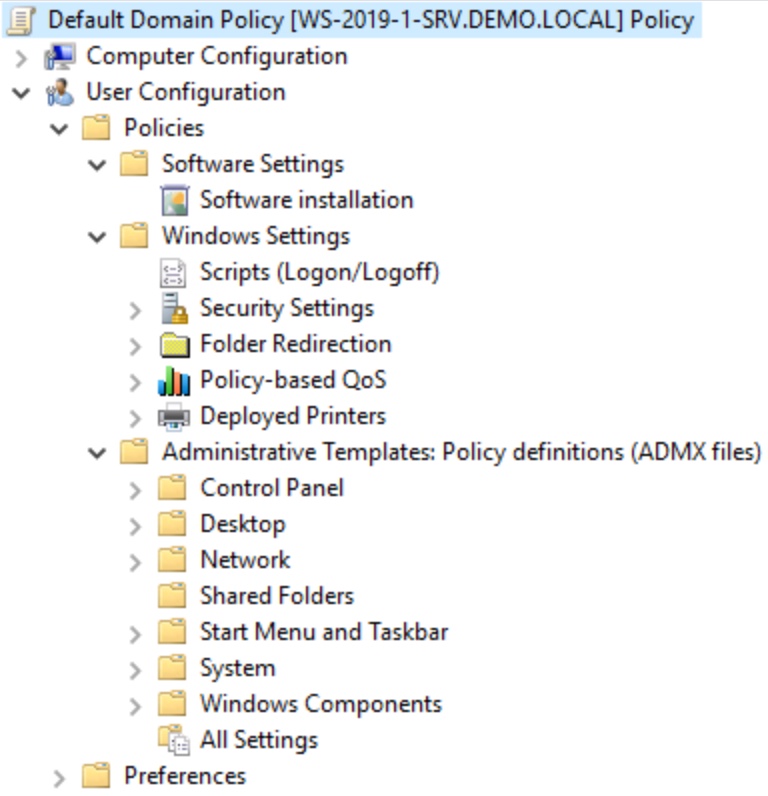
Figure 8: Group Policy console showing configuration management categories for users.
AD's ability to span campuses, regions or even the globe means that it satisfies the needs of the largest enterprises.
I'm not sure it's accurate to say AD has disadvantages. There are aspects of it to be aware of, however. AD incurs a cost and increases the complexity of your network environment. Not only will hardware and Windows licenses add up quickly, but so will the support costs of hiring staff or service providers to administer the domain. Don't forget that the staff will need periodic training to take advantage of the latest improvements. The numerous benefits offset these costs.
Active Directory Is an Essential Service
AD requires a careful design that must be periodically reviewed as technologies change. Its Group Policy configuration management tool is its own topic of expertise, with thousands of security and convenience settings available to provide users with exactly what they need. Finally, administrators must understand AD replication, especially in regional or larger deployments.
Active Directory is an incredible directory service system that underpins many of Microsoft's most popular products. It offers users a single sign-on experience and the flexibility to log on from any domain-based computer. It gives administrators a centralized administration point for managing users, devices, configurations, security options and more. With 23 years in the field, it's well-tested and an assumed feature of a modern Windows-based business network. Use the basic concepts and terminology above to begin learning this essential service.
CompTIA is here to support you throughout your IT career. Get free resources, career advice, and special offers on CompTIA training and certifications!

