CompTIA ITF+
IT Fundamentals (ITF+) is an introduction to foundational technology knowledge and skills.
Learn more Example questionsClick a career path and your experience level, and we'll show you the CompTIA certifications you need to get there!
IT Support Specialists are responsible for analyzing, troubleshooting and evaluating technology issues. This role may support internal clients, helping to keep employees productive, or external customers of a company, helping them via the telephone or webchat. Some specialists are tasked with giving instructions to customers on how to use business-specific programs or working with other technicians to resolve problems. Other specialists may be responsible for answering simpler questions from nonbusiness customers, like reestablishing internet connections or troubleshooting household IT products like Wi-Fi routers.
| Experience Level | Beginner | Intermediate | Advanced |
|---|---|---|---|
| Annual salary range* | $34,220 – $49,770 | $39,380 – $68,130 | $49,770 – $91,060 |
| Job Postings* | 135750 | 88610 | 24620 |
| Number of certificates available at each level | 3 CompTIA ITF+ CompTIA A+ ITIL | 4 CompTIA Network+ CompTIA Security+ ITIL Microsoft | 4 CompTIA Linux+ CompTIA Server+ ITIL Microsoft |
| Experience Level | Beginner | Intermediate | Advanced |
|---|
*CompTIA | Lightcast | U.S. Bureau of Labor Statistics
Note: Many employers don't specify any years of experience in job postings.
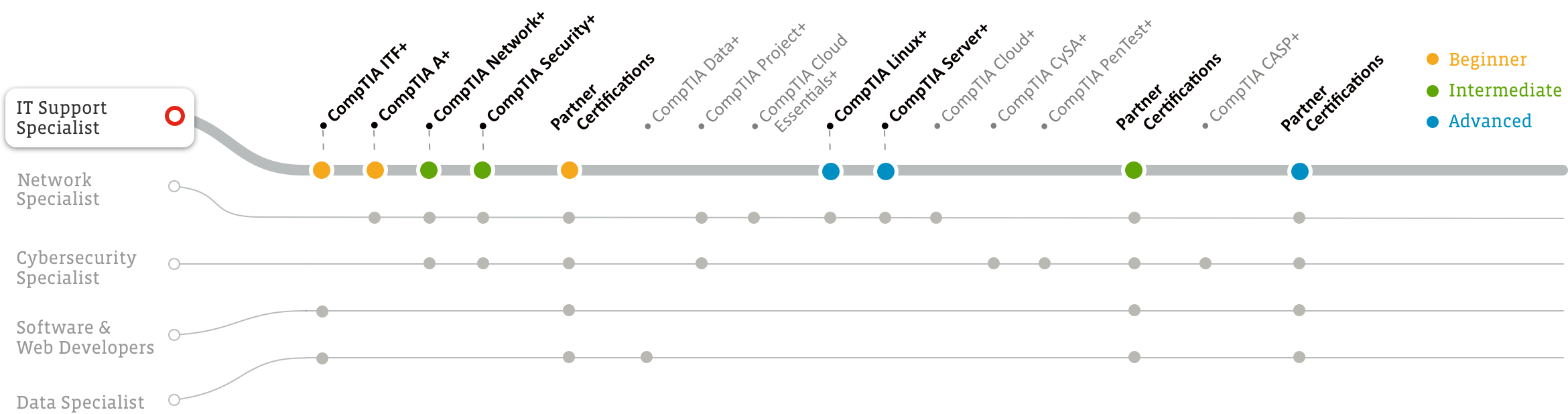
Certifications like CompTIA IT Fundamentals+ can give you the background in IT that you need if you don’t already have it, and CompTIA A+ can get your foot in the door as an IT Support Specialist.
IT Fundamentals (ITF+) is an introduction to foundational technology knowledge and skills.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
Core 1 (220-1001)
| 1.0 Software | 21% |
| 2.0 Hardware | 18% |
| 3.0 Security | 21% |
| 4.0 Networking | 16% |
| 5.0 Basic IT Literacy | 24% |
| Total | 100% |
Example Questions
A package-delivery service is working with address information, which contains a house number and a street name. What is the best data type to use for the house number?
A. Integer B. String C. Float D. CharWhy do laptops use a heat spreader instead of heatsinks in their cooling system?
A. Heatsinks are filled with liquid and not conducive to laptop mobility. B. Heatsinks require a lot of extra electricity to run. C. Heatsinks are bulky objects with a lot of height. D. Heatsinks are too expensive and reserved for high-end systems.A senior manager of a regional office branch needs a payroll report of all staff, to calculate next year's budget. Which program is NOT useful for that?
A. Spreadsheet software B. Database software C. Accounting software D. Project management softwareA website visitor realizes that an important notification is not showing because the browser has a pop-up blocker. What's the best thing to do?
A. Disable the pop-up blocker. B. Add an exception for this website. C. Use a different browser. D. Avoid visiting this website.What does this pseudocode declare?
declare MinutesPerHour as Number = 60
An attacker successfully connects to an open wireless access point, and proceeds to monitor and capture the plain text traffic on the network. Which of the following integrity concerns does this describe?
A. A Denial of Service (DoS) attack B. An impersonation attack C. A Man-in-the-Middle (MitM) attack D. A replay attackA+ is the starting point for a career in IT. The performance-based exams certify foundational IT skills across a variety of devices and operating systems.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
Core 1 (220-1001)
| 1.0 Mobile Devices | 14% |
| 2.0 Networking | 20% |
| 3.0 Hardware | 27% |
| 4.0 Virtualization and Cloud Computing | 12% |
| 5.0 Hardware and Network Troubleshooting | 27% |
| Total | 100% |
Core 2 (220-1002)
| 1.0 Operating Systems | 27% |
| 2.0 Security | 24% |
| 3.0 Software Troubleshooting | 26% |
| 4.0 Operational Procedures | 23% |
| Total | 100% |
Example Questions
You have been frequenting a local coffee shop with your Android tablet. While you are there, you use the free WiFi connection. With concern over the security of your browsing, you decide to take action. Which technology would address your concern the best?
A. VPN B. Antivirus C. Private IP D. WPA2You need to configure a SOHO (Small Office Home Office) network to be easily discovered by guest users. Which feature should be configured?
A. DNS (Domain Name System) B. DHCP (Dynamic Host Configuration Protocol) C. SSID (Service Set Identifier) D. MAC (Media Access Control) FilteringAn ordinary office environment needs computers that have multiple user account settings where each user is allocated private data storage. What type of workstations would you build for this environment?
A. Build a virtualization workstation. B. Build a thin client. C. Build a thick client. D. Build a CAM workstation.A support ticket has been assigned to you stating that the Engineers are complaining that their Computer Aided Design (CAD) application is displaying poorly. What do you do to upgrade these PCs and solve this problem?
A. Install more RAM. B. Install higher-end video cards. C. Install faster CPUs. D. Install Solid State Drives (SSDs).You need to setup a few virtual workstations for a network test lab. You have a computer to use as the host machine, however, it does not have an operating system installed. What is the easiest and quickest solution to configure the host system?
A. Install a type-2 hypervisor on the host machine and then install the guest operating systems. B. Install one of the guest operating systems to act as both the host and a guest operating system. C. Install a type-1 hypervisor on the host machine and then install the guest operating systems. D. Install Microsoft Virtual PC as it is free, and then install the guest operating systems.How can you fix a touchpad that is too sensitive, causing a ghost cursor and jumping about when typing?
A. Turn NumLock off on the external keyboard. B. Configure the input options. C. Replace the touchpad. D. Revert to an older driver version.CompTIA certifications establish a baseline foundation of skills that you can build upon with other vendor or technology-specific certifications.
Validate skills against a set of IT service management practices. ITIL certifications, managed by AXELOS, are awarded to individuals across four levels of competency:
Foundation
Managing Professional
Strategic Leader
Master
*CompTIA | Lightcast | U.S. Bureau of Labor Statistics
Note: Many employers don't specify any years of experience in job postings.

Certifications like CompTIA IT Fundamentals+ and CompTIA A+ can get your foot in the door as an IT Support Specialist. Adding CompTIA Network+ and Security+ can help you advance your career in IT Support.
Network+ certifies the essential skills needed to confidently design, configure, manage and troubleshoot wired and wireless networks.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
| 1.0 Networking Concepts | 23% |
| 2.0 Infrastructure | 18% |
| 3.0 Network Operations | 17% |
| 4.0 Network Security | 20% |
| 5.0 Network Troubleshooting and Tools | 22% |
| Total | 100% |
Example Questions
An office workstation receives an Internet Protocol version 4 (IPv4) address from a Dynamic Host Configuration Protocol (DHCP) server. The IP lease includes the default gateway address which is the address of the office's layer 3 switch. A network administrator confirmed network connectivity by pinging the gateway. At what layer of the Open Systems Interconnection (OSI) are these two devices communicating with each other when using the ping command?
A. Layer 3 - Network B. Layer 2 - Data Link C. Layer 6 - Presentation D. Layer 7 - ApplicationA manager informs a support technician that users spend too much time using company computers for personal reasons. Which of the following can the technician implement to address the issue?
A. UTM appliance B. Layer 7 firewall C. Content filter D. Smart jackA network consultant is doing IT contingency planning and is trying to identify likely points of failure for the network. Which of the following would the consultant identify as Single Points of Failure in need of upgrades for added redundancy? (Select all that apply)
A. There is a lack of a load balancing device. B. A backup power generator is available on-site. C. There is a single power supply for a critical server. D. The main server is set up for full backup operations.An employee uses a key fob that contains a chip with a digital certificate and authenticates a person through a reader. Which of the following types of authentication factors does this describe?
A. Something you know B. Something you have C. Something you are D. Something you doA network administrator purchased new network switches from a vendor. Upon receiving and installing them, what should the admin do to harden the device to ensure secure device configuration of the switches? (Select all that apply)
A. Change default usernames and passwords. B. Remove vendor-installed backdoors. C. Disable or close unused ports and services. D. Implement a common prevalent password.A user installs a financial software package that requires cloud access. For some reason, the application fails to connect to the cloud server. What caused this issue?
A. Duplicate IP (Internet Protocol) address B. Incorrect host-based firewall settings C. Incorrect time D. Unresponsive serviceSecurity+ provides a global benchmark for best practices in IT network and operational security, one of the fastest-growing fields in IT.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
| 1.0 Threats, Attacks and Vulnerabilities | 21% |
| 2.0 Technologies and Tools | 22% |
| 3.0 Architecture and Design | 15% |
| 4.0 Identity and Access Management | 16% |
| 5.0 Risk Management | 14% |
| 6.0 Cryptography and PKI | 12% |
| Total | 100% |
Example Questions
An attacker impersonates a member of the cleaning crew for a company's building, and requests an employee to hold the door open while the impersonator brings in a cleaning cart. The employee fell victim to what type of attack?
A. A lunchtime attack B. Shoulder surfing C. Piggy backing D. Dumpster divingThe DMZ (demilitarized zone) has a new virtual firewall server. A user reported that Internet websites are viewable, but no longer has a connection to an FTP (file transfer protocol) site. Which of the following is most likely the cause of the disconnection?
A. The user does not have access to the FTP site. B. A network cable disconnected from the server. C. The Firewall implicitly denied access to the FTP site. D. The ACL still requires setting up.A user has multiple documents to review, regarding a device from an authorized government vendor, with approval to use the documents. While attempting to send the documents to a personal email, to review later at home, the email returned with a message saying it failed to send. What is most likely the cause of this? (Select two)
A. Based on policy, the employee cannot use personal email. B. The DLP system flagged an incident. C. The antivirus software flagged the documents. D. The attachment file size is too large.After exploiting a vulnerability during testing, an administrator released a Security Update as a patch for Microsoft Internet Explorer. How should the administrator proceed in applying the patch?
A. Apply the patch directly to production. B. Apply the Security Update to the staging environment and test the system functionality. C. Wait for the quarterly update before patching the vulnerability. D. Apply the patch to the sandbox environment and test functionality.Fingerprint scanning is one of the most straightforward methods of biometric identification. Which of these concerns are most pertinent to the use of this technology?(Select two)
A. Ease of spoofing B. Surfaces must be clean and dry C. Revocability of credentials D. High expense of installationKey strength is based on length and randomness. One way to strengthen a key is to add a nonce or an Initialization Vector (IV). The same is true for passwords, which can be strengthened by adding a salt to a hashed password value. Evaluate the following to identify the statements that are true about nonces, IVs, and salts.(Select two)
A. The value of a nonce is hidden. B. A salt could be a counter value. C. Use of a salt ensures identical plaintexts produce different ciphertexts. D. Use of an initialization vector ensures identical plaintexts produce different ciphertexts.CompTIA certifications establish a baseline foundation of skills that you can build upon with other vendor or technology-specific certifications.
Validate skills against a set of IT service management practices. ITIL certifications, managed by AXELOS, are awarded to individuals across four levels of competency:
Foundation
Managing Professional
Strategic Leader
Master
Assess skills in using Microsoft technologies, including Azure, Dynamics 365, Microsoft 365 and Power Platform. Within each technology or role-based grouping, certifications are awarded across four levels:
Fundamental
Associate
Expert
Specialty
*CompTIA | Lightcast | U.S. Bureau of Labor Statistics
Note: Many employers don't specify any years of experience in job postings.

Certifications like CompTIA IT Fundamentals+ and CompTIA A+ can get your foot in the door as an IT Support Specialist. Adding CompTIA Linux+ and Server+ can help you advance your career.
Linux+ is an internationally recognized credential validating baseline competencies required for Linux administrators.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
| 1.0 Hardware and System Configuration | 21% |
| 2.0 Systems Operation and Maintenance | 26% |
| 3.0 Security | 19% |
| 4.0 Linux Troubleshooting and Diagnostics | 20% |
| 5.0 Automation and Scripting | 14% |
| Total | 100% |
Example Questions
You wish to view currently loaded kernel modules and their usage details. Which command will help you view this information?
A. modinfo B. rmmod C. lsmod D. insmodYou are implementing print management in a Linux environment. Which of the following would you use as a print server?
A. lpr B. lsusb C. CUPS D. udevadmVim is a modal editor and its different modes decide its functionality. Which one of the below is NOT one of the four Vim modes?
A. insert B. gedit C. execute D. visualYou deploy a public key infrastructure (PKI) in your organization. Which of the following components must be kept in a highly secure system where the risk of it being stolen is low?
A. Public key B. Private key C. Digital signature D. Self-signed certificateYou have just used the lprm 4 command. What type of problem are you trying to remedy?
A. Printing B. Memory C. Storage D. KeyboardYou are writing a Bash script and would like to connect multiple values together for evaluation. What type of operator should you use in this script?
A. Arithmetic B. String C. Comparison D. LogicalServer+ confirms the technical knowledge and skills required to support and secure server hardware and software.
Learn more Example questionsThe table below lists the domains measured by the full examination and the extent to which they are represented.
Domain and percentage of examination
| 1.0 Server Architecture | 12% |
| 2.0 Server Administration | 24% |
| 3.0 Storage | 12% |
| 4.0 Security | 13% |
| 5.0 Networking | 10% |
| 6.0 Disaster Recover | 9% |
| 7.0 Troubleshooting | 20% |
| Total | 100% |
Example Questions
Which form factor is measured in increments such as 1U, 2U and 4U?
A. Tower B. Rack mount C. Redundant Array of Independent Disks (RAID) D. BladeWhich management method uses a dedicated channel to manage servers and network devices typically using a network connection that is physically separated from the production network?
A. Server management plan B. In-band management C. Out-of-band (OOB) management D. Secure Shell (SSH)Which statement is true regarding solid state drives (SSDs)?
A. Solid state devices contain moving parts and tend to be less reliable than magnetic drives. B. Solid state devices contain no moving parts and tend to be more reliable than magnetic drives. C. Solid state drives are extremely fast because these devices store information on a magnetic coated media that is rotated under a read/write head. D. Solid state drives are fine for end users but should never be used in servers.How can you prevent attackers from connecting universal serial bus (USB) drives to the server?
A. Setting a basic input/output system (BIOS) password B. Disable unneeded hardware and physical ports and devices C. Disabling Wake on LAN D. Setting up the boot orderWhich is a feature of Internet Protocol version 6 (IPv6)?
A. Addresses are formatted with dotted decimal notation. B. It uses broadcast addresses. C. An address is 32 bits long. D. An address is 128 bits long.What type of analysis will help you determine the effect of a disruption to the business?
A. Disaster recovery plan B. Business continuity plan (BCP) C. Continuity of Operations (COOP) D. Business impactCompTIA certifications establish a baseline foundation of skills that you can build upon with other vendor or technology-specific certifications.
Validate skills against a set of IT service management practices. ITIL certifications, managed by AXELOS, are awarded to individuals across four levels of competency:
Foundation
Managing Professional
Strategic Leader
Master
Assess skills in using Microsoft technologies, including Azure, Dynamics 365, Microsoft 365 and Power Platform. Within each technology or role-based grouping, certifications are awarded across four levels:
Fundamental
Associate
Expert
Specialty
CompTIA offers everything you need to prepare for your certification exam. Explore training developed by CompTIA with options that fit various learning styles and timelines. Whether you prefer self-study or classroom training, CompTIA has you covered.